![Dotnet Core : What can you do in case you wish to authorize without [Authorize] ?](https://blog.honosoft.com/wp-content/uploads/2019/07/header-dotnet-authorize.jpg)
Dotnet Core : What can you do in case you wish to authorize without [Authorize] ?
In some cases, the [Authorize] attribute is not all you want. Sometimes, you wish that something else existed and that’s where the IAuthorizationFilter (or IAsyncAuthorizationFilter) come into play. Before going there, ensure that you don’t simply need a new Policy (See MSDN article or doc.). For more details about the Filter I will let you read the MSDN page which is always updated.
What we will cover here:
Ordering of the filters within Dotnet Core
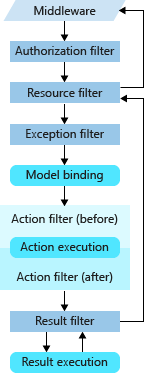
Basically, most of the time we want to add some behavior within the ActionFilter area. But when it comes to authorization, the best is to stop the entire pipeline as soon as possible. That’s where the IAuthorizationFilter comes into play.
Sample of creating an IAuthorizationFilter
IAuthorizationFilterThe IAuthorizationFilter only require us one method to implement (i.e.: OnAuthorization). There is also no need of doing any dependency injection for such attribute in order to activate it. The following code is only an example doing nothing special, but you should grasp the idea.
public sealed class SpecialAuthorizeAttribute : Attribute, IAuthorizationFilter // or IAsyncAuthorizationFilter ...
{
private const string HEADER_SPECIAL_STUFF = "specialHeaderStuff";
public void OnAuthorization(AuthorizationFilterContext context)
{
if (context != null)
{
var authCode = context.HttpContext.Request.Headers[HEADER_SPECIAL_STUFF];
// Write your logic here.
if (string.IsNullOrEmpty(authCode))
{
context.Result = new UnauthorizedObjectResult($"{HEADER_SPECIAL_STUFF} is required");
return;
}
if (!authCode.Equals("IAmValid"))
{
context.Result = new UnauthorizedObjectResult($"{HEADER_SPECIAL_STUFF} is invalid");
return;
}
// ===== if you're here, it's a success =====
// DO STUFF
//
// ===== you can also use registered services =====
// var someService = context.HttpContext.RequestServices.GetService<ISomeService>();
}
}
}
Sample of using our custom IAuthorizationFilter
The following code is based on a new WebApi project.
[Route("api/[controller]")]
[ApiController]
public class ValuesController : ControllerBase
{
// GET api/values/5
[SpecialAuthorize]
[HttpGet("{id}")]
public ActionResult<string> Get(int id)
{
return "value";
}
// ... other stuff
}
In order to execute, you can simply do a HTTP call using Curl.
nordes@Something:~$ curl https://localhost:5001/api/values/1 --insecure && echo '' specialHeaderStuff is required nordes@Something:~$ curl https://localhost:5001/api/values/1 -H 'specialHeaderStuff:IAmInvalid' --insecure && echo '' specialHeaderStuff is invalid nordes@Something:~$ curl https://localhost:5001/api/values/1 -H 'specialHeaderStuff:IAmValid' --insecure && echo '' value
As you can see, when I use a Valid value, it is accepted and then process the Controller-Action. The attribute could also be put on the Controller and in such case will apply that rule to every actions.
Conclusion
As you can see, it’s not something complex to do. What you should ask yourself is if you need to use it? In my case, I had to use it for specific scenario, but most people will probably simply use the policy over the official Authorize attribute given by the framework.

Quel est le meilleur encodeur PHP en termes de vitesse et de sécurité, j’ai testé PHPGuarder et c’est bon, et d’autres que j’ai testés sont lents